This computer virus has spread to over 200,000 victims in 150 countries and regions.
Cctv newsThe first thing many people do when they go to work recently is to disconnect the network, install security software, fix patches, and then plug in the network cable to work, in order to prevent the menacing malicious blackmail computer virus — — I want to cry.
"Want to cry" has swept the world over the weekend, and its scale and influence are called "unprecedented". In the coming week, the harm of the virus may accelerate its spread.
Ransom software makes the world "want to cry"!
Japan’s NHK TV reported on the 15th that Hitachi Group’s server was attacked by ransomware "Want to Cry", which caused a failure when sending and receiving emails. On the same day, Sputnik reported that Renault, one of France’s largest automobile manufacturers, closed its factory in northern France. Previously, several factories in Renault had stopped production due to cyber attacks.
On 14th, Wayne Wright, head of Europol, said that the cyber attack had reached an "unprecedented level".According to the latest statistics, more than 200,000 users in at least 150 countries and regions have been attacked, and most of the victims are commercial users, including many large enterprises.With the arrival of a new round of working days on the 15th, this data is likely to continue to climb.

The ransomware attack began on the 12th of this month. Some hospitals in Britain were the first to be attacked by viruses. Many patients were unable to see a doctor in time, and routine operations were temporarily cancelled. The German railway system was attacked, which affected many people’s travel plans. Many computers in the headquarters of Telefó nica, the Spanish telecom giant, have also been paralyzed. In addition, Russia, China and other countries have also suffered large-scale ransomware attacks.
What are the symptoms of the computer?
After being infected by ransomware, computer files will be encrypted and locked, and can only be decrypted and restored after paying ransom. These files may be deleted if the ransom is not paid. The ransom demanded is virtual currency — — Bitcoin. Due to the lack of identity information supervision, it is difficult to track online transactions of Bitcoin.
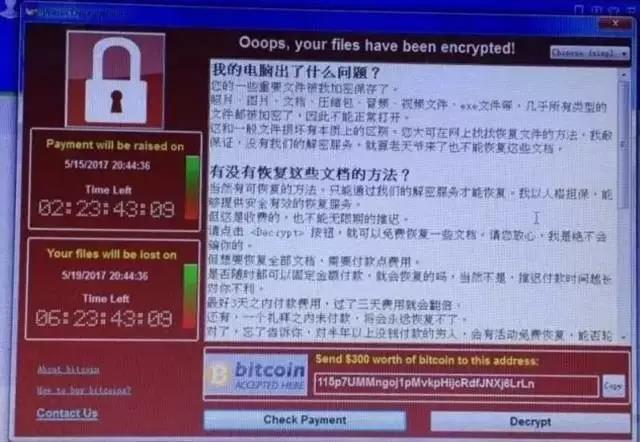
The Guardian reported on the 14th that a company tracking illegal activities on the Internet has locked three related bitcoin accounts, but because the ransom has not been withdrawn, it is impossible to lock the behind-the-scenes manipulation of cybercrime. At present, cyber attackers have received tens of thousands of dollars in "ransom", and the ransom may be further increased.

The US National Security Bureau was accused of being the culprit.
The media pointed the finger at the National Security Agency. The report said that hackers were able to trigger a global virus crisis because they used the super "cyber weapons" of American intelligence agencies.
The National Security Agency (NSA) is the largest intelligence department in the U.S. government agencies, which is responsible for collecting and analyzing foreign and domestic communication materials and belongs to the U.S. Department of Defense. Headquartered in fort meade, Maryland, it is hidden in a forest, larger than the CIA headquarters, and is known as the "mysterious maze".
The Financial Times reported that the hacker used the Windows hacking tool "Eternal Blue" independently designed by the National Security Bureau of the United States. In April this year, the hacker organization "Shadow Broker" disclosed a batch of hacking tools of the National Security Bureau on the Internet, including the vulnerability tool "Eternal Blue" that may have been leaked last year.

The American media ridiculed that the cyber weapons developed by the US National Security Bureau were "civilian". Chief law officer brad smith, president of Microsoft Corporation, described it as the theft of some Tomahawk cruise missiles of the US military. Edward snowden, the exposer of the "Prism" monitoring project, wrote on Twitter on the 12th that the US National Security Bureau had developed a dangerous attack tool despite warnings.
In March this year, Reuters quoted an official from the National Security Agency as saying that more than 90% of the funds spent by the United States on network projects were used for cyber attacks, such as developing computer intrusion systems and eavesdropping on communications. Another network security expert believes that using more resources for attack rather than defense makes Internet users face greater risks.
In the face of outside criticism, the US National Security Bureau has not yet responded.
Precautions: Turn on the computer and make security patches after disconnecting the network.
This virus attack is mainly aimed at the vulnerability of Microsoft Windows. In view of the seriousness of the situation, Microsoft quickly announced the adoption of unusual security measures to provide patches for some "old Windows" platforms that are no longer supported.
In order to avoid being infected by the virus, experts suggest that users should disconnect the network and turn it on, that is to say, unplug the network cable before turning it on, which can basically avoid being infected by ransomware. After starting up, you should try to put on security patches as soon as possible, or install defense tools launched by various network security companies for this matter before you can connect to the internet.

According to experts, there is no way to open the locked files of infected computers. There is a rumor on the Internet that the author of ransomware has released the key, but it has been proved that this is false news. It is not recommended that the victim pay the ransom according to the hacker’s request, because it is impossible to determine the true intention of the communicator at present, and paying the ransom may not necessarily receive the key needed for unlocking.